Cyber Security: Ransomware & Crypto Viruses
Brief history of Ransomware
Ransomware has been around for years in various forms. It was reported that the first example of Ransomware was in America in 1989. Fast forward to today and it is estimated that there are around a million different types of ransomware.
In recent times it has become more and more common to have been affected by the various types of ransomware. Security experts have warned that it’s the fastest growing form of computer virus globally.
There are different types of Ransomware, and over recent years they have become more sophisticated and have evolved to the point where it is the cyber criminals’ preferred method of attack as the success rates are so high.
To demonstrate this, in 2015 72% of business surveyed had experienced ransomware incidents whilst in 2013 it was only 14%. In 2016 the government invested £1.9bn to protect the UK against Cyber breaches and attacks but businesses must do more to protect themselves and cannot be reliant on the government to protect them.
So what is Ransomware?
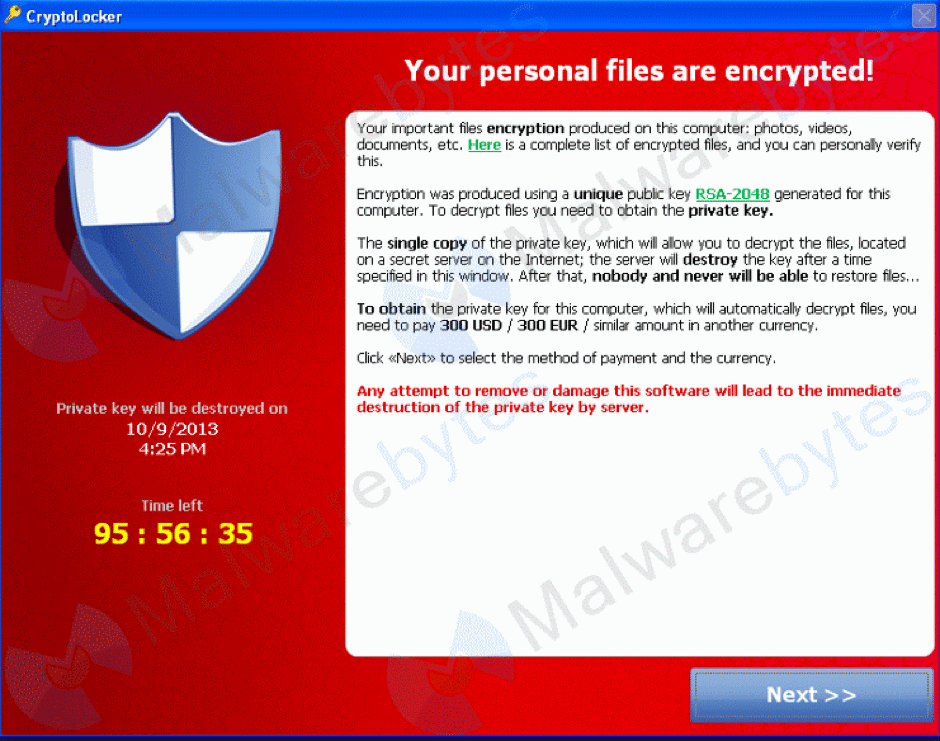
Ransomware is essentially a virus that is installed on your device and unbeknown to you it is encrypting your data in the background whilst you are happily working away. This malicious virus locks the individual out of their computer files and demands a fee for them to be returned, hence the name ransomware. This is an example of the CryptoLocker virus in action. You will notice from the below there is a ‘time left’ count down which is reducing in real time. When this reaches zero, your encryption key is destroyed and your data is then irretrievable. That’s not strictly true as what the criminals often do is give you a ‘final chance’ to pay which is often considerably more than what they were originally asking for.
What is encryption you may ask?
In simple terms, encryption is what keeps your data safe and secure on the internet. For example, when you are using internet banking, your data is encrypted so nobody can steal your data and gain access to your bank accounts. AES encryption is predominantly used and has been in place for around the last twenty years. Once data is encrypted with this, it is impossible to gain access to the data without the encryption key. Cyber criminals are now using this same technology to encrypt the data of individuals and businesses to then hold them to ransom by forcing them to pay to retrieve their data. If you don’t pay them, you will lose your data.
Who are the cyber criminals targeting?
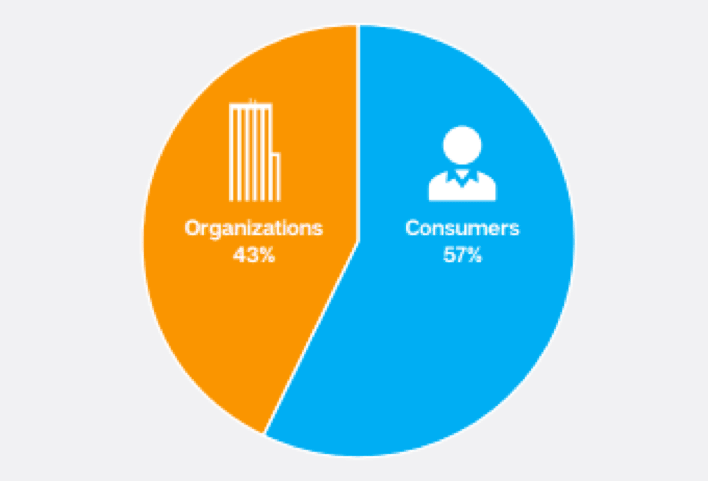
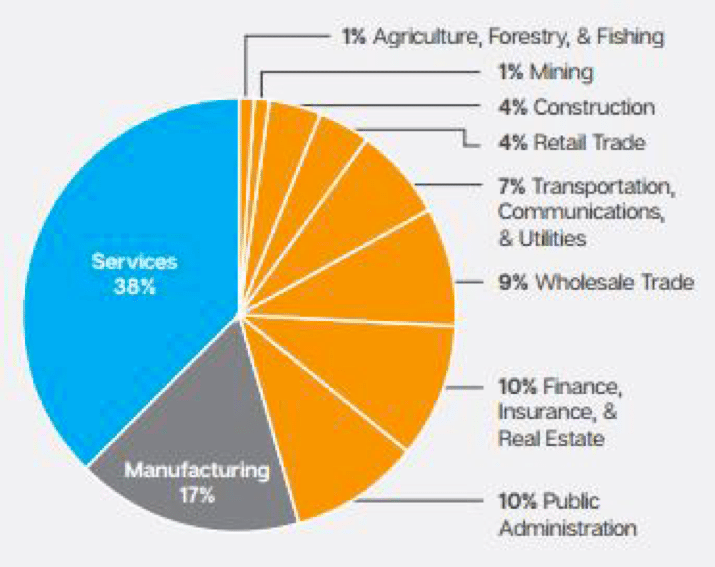
In short, everyone. Businesses are seen to be a better target as they are more likely to have data which could be stolen and if infected they are potentially more likely to pay the ransom. Equally, consumers are a target as they often have unsecured devices and are not aware that such threats exist. The below left demonstrates reported infections from January 2015 to April 2016 whilst the below right demonstrates infections by sector for the same period.
How does the virus get there in the first place?
Like many computer viruses, ransomware often arrives in the form of phishing tactics (scammers tricking you), emails with attachments and links that contain the virus and often fake software updates which again contain the virus. Ransomware can also arrive by simply browsing a website.
Once the process starts, there is no stopping it and once all files have been encrypted it demands a fee. If you suspect you may have inadvertently been infected by ransomware, disable your WiFi connection or unplug your device from the network as an active internet connection is required to complete the encryption.
Why are the criminals doing this?
To make money! And it’s into the billions. There is also the status and prestige the criminals feel they get in return for infecting a major business and taking down their website, network or systems. An example of this is the Texas Police Department being targeted with ransomware which resulted in losing eight years of digital evidence.
How do they get paid?
Usually cyber criminals request payment in bitcoins. In simple terms bitcoins are electronic currency otherwise known as Cryptocurrency. The reason criminals use bitcoins is because it is incredibly difficult for the authorities to trace bitcoin transactions and where they actually end up. The reason for this is because bitcoins pass through tens of thousands of computers before they reach their destination.

What can I do to prevent this from happening to me? 10 Top Tips
The threat is serious and is costing businesses tens of thousands of pounds. Some businesses have ceased to trade as they have lost all of their data. There are many things that you can do to prevent this happening to you and your business:
1. Ensure you have a daily backup that includes all of your data set so in the event you are targeted, you don’t have to pay as the virus can be removed and data restored. Don’t backup to USB storage as when the virus runs this will infect the backup too. Ensure this is managed daily as all too often we have seen companies completing daily backups that aren’t being checked, to find in their hour of need that the backup has been failing for the last six months.
2. Software protection tools can be used to stop the virus running in the first instance which blocks the executable virus from running – this is generally technical and you may need to seek advice from an expert.
3. Use an antivirus solution that encompasses locker prevention tools built into the software and ideally one that is managed and monitored by your IT support company.
4. Implement strict security policies and complex passwords so you are well protected and your systems are secure.
5. Implement content filtering that reduces the likelihood of your staff accessing rogue websites containing such viruses.
6. Implement email policies that remove links and attachments that contain malicious content.
7. Ensure that your devices are fully patched with the latest software updates so you are fully protected.
8. Move data and services to the Cloud which is better protected and more secure.
9. Ensure you have a disaster recovery plan that details what to do in a situation where you have become infected.
10. Lastly, educate your workforce to ensure that they understand the threats and the impact they have, along with what to look out for. Never open attachments or click links unless you know that the sender is legitimate and genuine.
If you would like any further information to help secure your business and its data then contact San-iT where we will be happy to provide advice at no cost. www.San-iT.co.uk 0161 359 3689





